
Step 1 : Update System Repositories
yum update
Step 2 : Upgrade System Repositories
yum upgrade
Step 3 : Installaton Of Nginx Web Server
yum install nginx
Step 4 : Enable The Nginx Service
systemctl enable nginx
Step 5 : Start Nginx Service
systemctl start nginx
Step 6: Check Status Of Nginx Service
systemctl status nginx
Congratulations! You have made it!
Allow Webserver To Listen System Ports.
Example : Web Server Uses Ports 80 (http) , 443 (https)
Step 1: Check the status of your firewall.
firewall-cmd --state
Step 2: To Know The Active Network Adapters Present In Your System.
firewall-cmd --get-active-zones
Output:
libvirt interfaces: virbr0 public interfaces: enp0s3
Step 3: Temporarily Open port 80(http) and port 443(https) port.
firewall-cmd --zone=public --add-service=http
firewall-cmd --zone=public --add-service=https
Note, the above firewald commands will open http and https port only Temporarily.
Step 4: Permanently Open port 80(http) and port 443(https).
firewall-cmd --zone=public --permanent --add-service=http
firewall-cmd --zone=public --permanent --add-service=https
firewall-cmd --reload
Note, the above firewald commands will open http and https port Permanently.
Step 5: Check for open ports/services.
firewall-cmd --list-all
Output:
public (active) target: default icmp-block-inversion: no interfaces: enp0s3 sources: services: http https ports: protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules:
Step 6: In case you need to close the previously open HTTP port 80 and HTTPS port 443 execute:
firewall-cmd --zone=public --permanent --remove-service=http
firewall-cmd --zone=public --permanent --remove-service=https
firewall-cmd --reload
Step 7: To Know Nginx Listening Ports
netstat -ltnp | grep nginx
Output:
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 40143/nginx: master
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 40143/nginx: master
tcp6 0 0 :::80 :::* LISTEN 40143/nginx: master
tcp6 0 0 :::443 :::* LISTEN 40143/nginx: master
Step 8: To Know Nginx Listening Processes:
ps aux | grep nginx
Congratulations! You have made it!
Path /etc/nginx/nginx.conf -> This is The Main File Pointing To Your Public/Static IP/Local or Dynamic IP(DHCP)
* Choose Editor To Edit The File
Example: vim,vi,nano,gedit (i’m Using vim editor)
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024;
}
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
# Modified - 1
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
include /etc/nginx/mime.types;
default_type application/octet-stream;
# Load modular configuration files from the /etc/nginx/conf.d directory.
include /etc/nginx/conf.d/*.conf;
# Modified - 2
include /etc/nginx/sites-enabled/*.conf;
server_names_hash_bucket_size 64;
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name _;
root /usr/share/nginx/html;
# Load configuration files for the default server block.
include /etc/nginx/default.d/*.conf;
location / {
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
# Modified - 3
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
# server_name _;
server_name 202.153.32.18;
return 301 https://www.learnlinux.com$request_uri;
root /var/www/learnlinux.in/html;
ssl_certificate "/etc/letsencrypt/live/learnlinux.in/fullchain.pem";
ssl_certificate_key "/etc/letsencrypt/live/learnlinux.in/privkey.pem";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers PROFILE=SYSTEM;
ssl_prefer_server_ciphers on;
# Load configuration files for the default server block.
location / {
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
}
Create Directory in
cd /etc/nginx/
mkdir sites-available
mkdir sites-enabled
cd /etc/nginx/sites-available
vim learnlinux.in.conf
ln -s /etc/nginx/sites-available/learnlinux.in.in.conf /etc/nginx/sites-enabled/learnlinux.in.conf
nginx -t
systemctl restart nginx
Configuration Of Virtual Domain vim /etc/nginx/sites-available/learnlinux.in.conf
server {
server_name learnlinux.in www.learnlinux.in;
root /var/www/learnlinux.in/html/
index index.html index.htm index.php
error_log /var/www/learnlinux.in/learnlinux.in.error;
access_log /var/www/learnlinux.in/learnlinux.in.access;
location / {
}
error_page 404 /404.html;
location = /404.html {
root /var/www/learnlinux.in/html/;
internal;
}
location ~ /.well-known/acme-challenge {
allow all;
}
location ~ ^/(README|INSTALL|LICENSE|CHANGELOG|UPGRADING)$ {
deny all;
}
location ~ ^/(bin|SQL)/ {
deny all;
}
# A long browser cache lifetime can speed up repeat visits to your page
location ~* \.(jpg|jpeg|gif|png|webp|svg|woff|woff2|ttf|css|js|ico|xml)$ {
access_log off;
log_not_found off;
expires 360d;
}
}Wild Card *.example.in Positive SSL Certificate
yum install certbot
To Check Certbot Version
certbot --version
To Get Wildcard Certificate
sudo certbot certonly --manual -d *.learnlinux.in -d learnlinux.in --agree-tos --no-bootstrap --manual-public-ip-logging-ok --preferred-challenges dns-01 --server https://acme-v02.api.letsencrypt.org/directory
The command options above are explained below:
- certonly: Obtain or renew a certificate, but do not install
- –manual: Obtain certificates interactively
- –preferred-challenges=dns: Use dns to authenticate domain ownership
- –server: Specify the endpoint to use to generate
- –agree-tos: Agree to the ACME server’s subscriber terms
- -d: Domain name to provide certificates for
Add Following Columns To Your DNS Server
A @ Static-IP 1 Hour
A * Static-IP 1 Hour
CNAME www @ 1/2 Hour
NS @ ns61.domaincontrol.com 1 Hour
NS @ ns62.domaincontrol.com 1 Hour
SOA @ Primary nameserver: ns61.domaincontrol.com. 1 Hour
TXT _acme-challenge Value 1/2 Hour
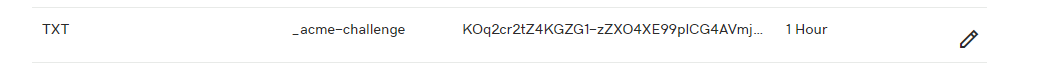
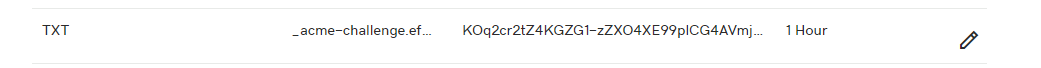
TXT _acme-challenge.example.in Value 1/2 Hour
To verify that the certificate is ready, run the commands below:
sudo certbot certificatesYou’re all set!
Now, Let’s Encrypt’s certificates are valid for 90 days… You’ll want to setup a crob job to automate the renewal process… To do that, open crontab and add the entry below:
sudo crontab -e
Then add the line below and save…
0 1 * * * /usr/bin/certbot renew >> /var/log/letsencrypt/renew.log
Save and you’re done!
Congratulations! You have successfully learned how to generate Let’s Encrypt wildcard certificates…
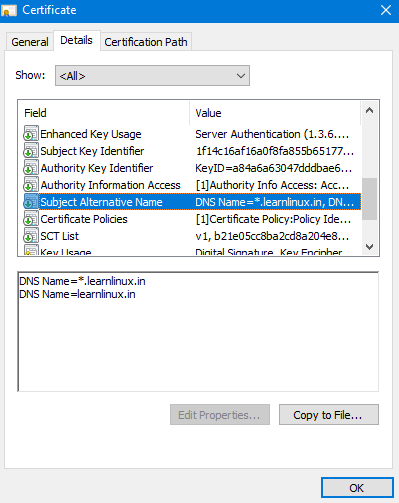
Certificate File Location /etc/letsencrypt/live/(example.in) <– domain.in or .com or .net or .in or .org
Now Add Certificate Files To nginx Configuration File /etc/nginx/sites-available/learnlinux.in.conf –> Server Block Done.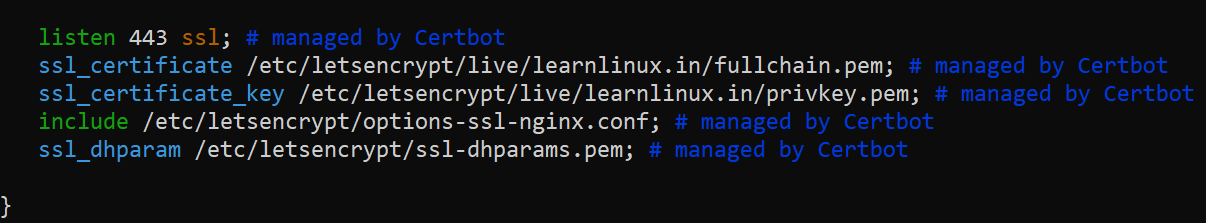
yum install php-fpm
systemctl enable php-fpm
systemctl start php-fpm
cd /etc/php-fpm-d/ -> vim www.conf
user nginx
group nginx
Step 3 :
listen = 127.0.0.1:9000
(Or)
Step 4:
listen = /run/php-fpm/www.sock
listen.allowed_clients = 127.0.0.1
Add Following Code in Nginx Configuration File If You Use Step 3:
location ~ \.php$ {
try_files $uri =404;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include fastcgi_params;
}Add Following Code in Nginx Configuration File If You Use Step 4 :
location ~ \.php$ {
try_files $uri =404;
fastcgi_pass unix:/run/php-fpm/www.sock;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include fastcgi_params;
}For Step 3 Checking Listening port :
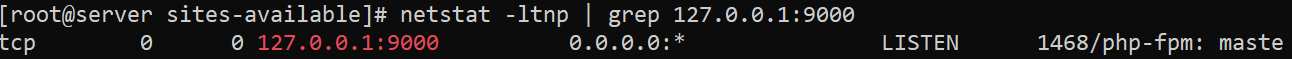
netstat -ltnp | grep 127.0.0.1:9000
server {
server_name learnlinux.in www.learnlinux.in;
client_max_body_size 100M;
root /var/www/learnlinux.in/html;
index index.php index.html index.htm;
error_log /var/www/learnlinux.in/learnlinux.in.error;
access_log /var/www/learnlinux.in/learnlinux.in.access;
location ~ \.php$ {
#try_files $uri =404;
#fastcgi_pass unix:/run/php-fpm/www.sock;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include fastcgi_params;
}
error_page 404 /404.html;
location = /404.html {
root /var/www/learnlinux.in/html/;
internal;
}
# Don't allow pages to be rendered in an iframe on external domains.
add_header X-Frame-Options "SAMEORIGIN";
# MIME sniffing prevention
add_header X-Content-Type-Options "nosniff";
# Enable cross-site scripting filter in supported browsers.
add_header X-Xss-Protection "1; mode=block";
# Enable Wordless Permananent Links
location / {
try_files $uri $uri/ /index.php?$args;
}
# Prevent access to certain file extensions
location ~\.(ini|log|conf)$ {
deny all;
}
location ~ /.well-known/acme-challenge {
allow all;
}
location ~ ^/(README|INSTALL|LICENSE|CHANGELOG|UPGRADING)$ {
deny all;
}
location ~ ^/(bin|SQL)/ {
deny all;
}
# A long browser cache lifetime can speed up repeat visits to your page
location ~* \.(jpg|jpeg|gif|png|webp|svg|woff|woff2|ttf|css|js|ico|xml)$ {
access_log off;
log_not_found off;
expires 360d;
}
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/learnlinux.in/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/learnlinux.in/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = learnlinux.in) {
return 301 https://www.$host$request_uri;
} # managed by Certbot
if ($host = www.learnlinux.in) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
server_name learnlinux.in www.learnlinux.in;
return 404; # managed by Certbot
}




More Stories
Squid Proxy
Firewall
Zimbra Troubleshooting